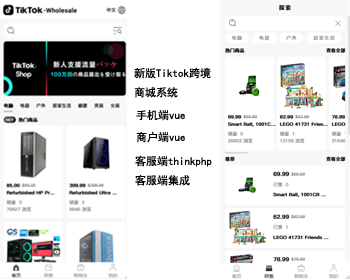
A few days ago, the server has been running bandwidth running full, thought it was a large flow did not pay attention to, and later found that it seems to be invasion control to different servers to send packets, only to know that there is a loophole, and later found One Soft Blind Box V2 version of the exhaust, is the use of the old framework version, the following to do an emergency repair tutorial!
![Image [1]|Tencent Cloud reports website has ThinkPHP 5.0.22 remote code execution high-risk vulnerability fixes](https://www.99blog.cn/wp-content/uploads/2023/05/e292e4d377115431.png)
Just solved a ThinkPHP <5.0.24 Request.php remote code execution vulnerability, One Soft Blind Box V2 there is a remote vulnerability problem!
ThinkPHP 5.0-5.0.23, 5.1.0-5.1.31 & & 5.2.* Full Version Remote Code Execution Vulnerability Handbook
http://blog.nsfocus.net/thinkphp-5-0-5-0-23-rce/Another ThinkPHP 5 <=5.0.22 Remote Code Execution High Risk Vulnerability What to do? See below for the solution!
- Open your website and go to the root directory. Follow this path to the thinkphp\library\think\App.php file.
- Mine is on line 553 everyone may be different, you can search for it exactly
$controller = strip_tags($result[1] ? : $config['default_controller']);3. Then insert after this line:
if (!preg_match('/^[A-Za-z](\w|\.) *$/', $controller)){
throw new HttpException(404, 'controller not exists:' . $controller);
}![Image [2]|Tencent Cloud reports website has ThinkPHP 5.0.22 remote code execution high-risk vulnerability fixes](https://www.99blog.cn/wp-content/uploads/2023/05/8dad8ebb20120058.png)
![Image [3]|Tencent Cloud reports website has ThinkPHP 5.0.22 remote code execution high-risk vulnerability fixes](https://www.99blog.cn/wp-content/uploads/2023/05/cadc6b94cb120720.png)
Thanks for visiting, get more great articles please bookmark this site.



![One Soft AI Star] ChatGPT V7.0 full open source JAVA intelligent AI robot openai open source unencrypted genuine soft writings | Jinan One Soft Network Technology](https://www.99blog.cn/wp-content/uploads/2023/04/6deaa2a89c160026-300x300.jpg)


![One key deployment tutorial] anonymous letter build / novice 1 minute on-line build anonymous letter / Pagoda one key rapid deployment / a letter source code rapid deployment | Jinan One Soft Network Technology](https://www.99blog.cn/wp-content/uploads/2022/08/b99a030f33000949-300x54.png)